What You Need to Know About the Newly Released 18 Center for Internet Security (CIS) Controls

The Center for Internet Security (CIS) recently released version eight of its controls, consolidating the previous 20 controls into 18. This latest list is organized by activity, rather than by who manages the device.
Why is this a big deal? To answer this, all you need to do is look at the number of data breach articles that fill news sites. From now until 2025, cybercrime is expected to cost the world more than $10.5 trillion per year, according to Cybercrime Magazine. In other words, the cost of not having a comprehensive cybersecurity program could be detrimental to any organization—regardless of the company’s age or size.
That’s where these controls come in. They represent a set of standardized best practices to safeguard data and protect against cyberattacks. Together, they establish a foundation on which companies of all sizes can build, mature, and maintain solid cybersecurity programs.
Welcome to Our 4-part Blog Series on CIS Controls
We did the research and will be breaking down all 18 CIS controls over the course of four blog posts throughout the month of October. We’ll start today by giving you a high-level snapshot of all 18 controls at once, then breaking them into smaller groups, allowing you to focus on a handful of controls at a time. Each forthcoming blog will explore six different controls, why each is important, and how you can easily weave them into your cybersecurity program. Here’s how we’re breaking it up:
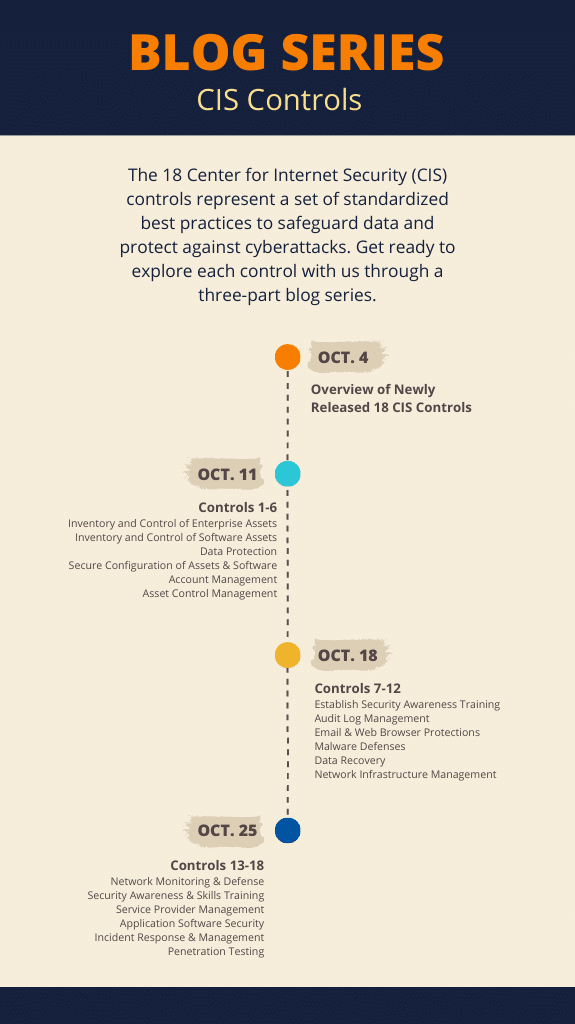
Every business is unique, so come along with us as we explore how to use each control to better secure your company’s most valuable asset—data.
Check back on Oct. 11 as we dive into Controls 1-6.
And remember you’re not in this alone. Working with a cybersecurity partner, like BARR Advisory, can help ensure your organization is secured from top to bottom. Contact us if you need assistance in understanding or implementing any of these controls within your own organization.